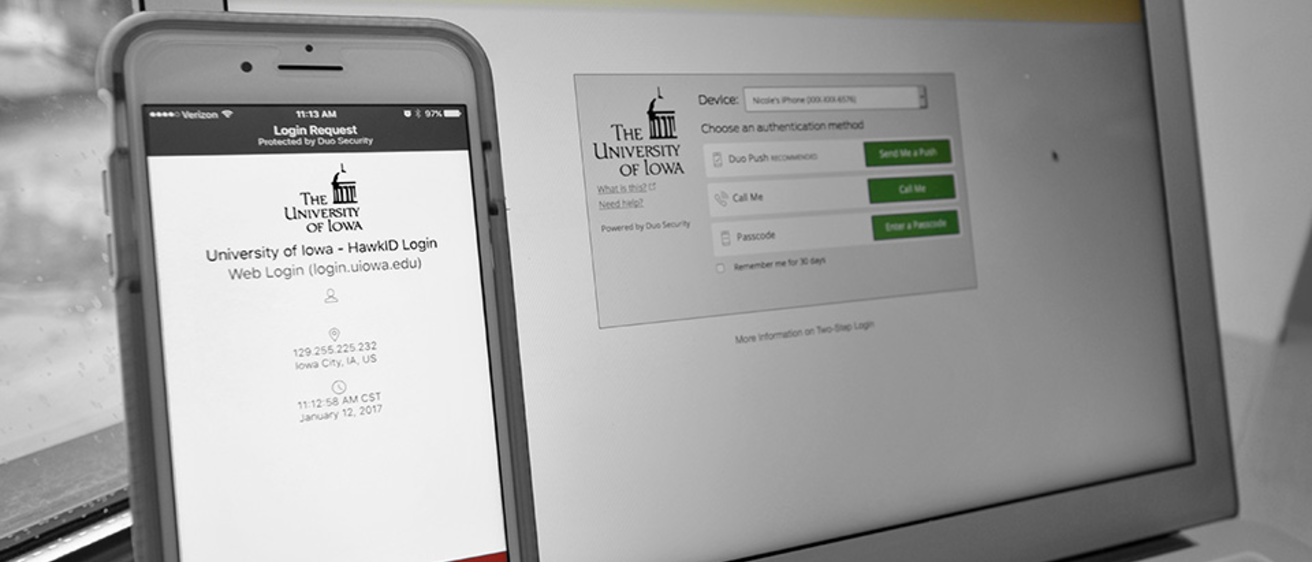
Starting in early 2018, UI faculty and staff will need to use two-step login when accessing MAUI and ICON, a measure designed to protect student information and academic records.
Manage your two-step login profile options from any campus computer at https://apps.its.uiowa.edu/uip-tools/two-step.
To make changes from off campus, call the ITS Help Desk at 319-384-4357.
Learn more about two-step login...
MAUI will require two-step login starting Jan. 2, ICON starting Feb. 5.
“We’re gradually rolling out this change in order to give faculty and staff time to adjust,” says Jane Drews, UI chief information security officer. “As our two key academic applications, MAUI and ICON demand the best available security. We also want to make the transition as smooth as possible for instructors who use ICON in the classroom.”
Faculty and staff already use two-step login when logging into Employee Self-Service. It’s been available on an opt-in basis for MAUI and ICON since the summer of 2017.
Students won’t be required to use two-step login when accessing ICON or MyUI (the student portal to MAUI), but they’re encouraged to opt in.
Ensuring classroom access
Two-step login uses two-factor authentication to prevent unauthorized users from breaking into accounts using stolen passwords.
To access a protected application, authorized users enter their HawkIDs and passwords. They then complete the login process using their phones, a pre-generated list of pass codes, or a token device that creates a one-time code.
Mobile phones equipped with the Duo Mobile app are the most popular (and recommended) option. Users complete their logins by approving “push” notifications sent to the app with a single tap. This eliminates the need to type in a pass code to complete the second login step.
Realizing that phone-based methods aren’t always practical, Information Technology Services has developed login options for virtually every scenario. Key fob token devices, for example, can generate individualized pass codes without a phone or network connection.
Balancing security and convenience
The enhanced login security measure was expedited to respond to incidents where unauthorized users changed grades in ICON using stolen HawkIDs and passwords; it balances the need for user security and convenience.
“At the end of the spring semester, we’ll evaluate faculty and staff experiences and exception requests, and look for potential improvements,” Drews says. “Adding a step to the login process is a modest tradeoff for keeping academic records accurate.”