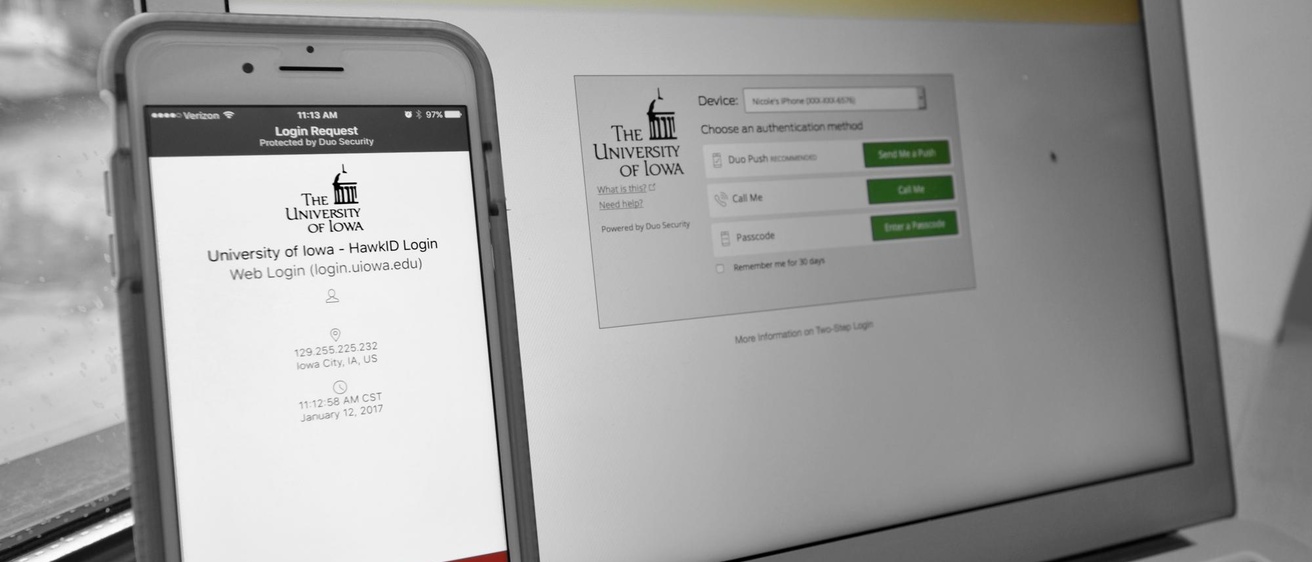
In the latest step in the University of Iowa’s continual efforts to strengthen its cybersecurity, all employees will need to use Two-Step Login to access the Employee Self Service website starting Feb. 22.
Two-factor authentication enhances security because in order to gain access to sensitive data and systems, you must provide your HawkID and password and then verify your identity with something only you have in your possession, like a cell phone, office phone, or single-use codes generated in advance.
This second step prevents criminals from accessing a host of private information in Self Service—tax forms and paycheck direct deposit preferences, to name a couple—if a HawkID and password were ever compromised. Criminals sometimes steal those credentials through phishing-email or phone scams, or when people reuse usernames and passwords to access external websites with security vulnerabilities.
“Two-Step Login protects your access to sensitive and critical applications because the second login step proves it’s you, not an attacker,” says UI Chief Information Security Officer Jane Drews.
Instructions for enrolling
Signing up takes only minutes. Employees can enroll at apps.its.uiowa.edu/uip-tools/two-step from a campus computer or by clicking “Manage Duo Two-Step Login” on the personal tab of Employee Self Service.
Instructions for enrollment and tips are available at its.uiowa.edu/two-step. Common questions are addressed under the “How to and Support” tab.
If you need extra assistance, contact the ITS Help Desk or reach out to your local IT support professionals.
UI Health Care employees: Please note that the hospital is also implementing Two-Step Login with Duo Security for UI Health Care accounts on remotely accessible applications. Enrollment of a Health Care account for Two-Step Login uses a separate process. For questions about UI Health Care account enrollment, contact the HCIS Help Desk: hcis.healthcare.uiowa.edu.
Employee Self Service, then, is a key online gateway to safeguard because it’s the portal to UI human resources and administrative records, such as payroll, benefits, time cards, training, personnel files, emergency contacts, and forms routed for approvals. Going forward, Two-Step Login will be expanded to more web applications that use a HawkID login. Integrations with other applications will be prioritized based on risk.
Duo Mobile app recommended
Two-Step Login is easy to use. Though almost any phone can be used to complete the second step (or single-use codes can be generated in advance), the Duo Mobile app is the quickest, simplest method. After entering your HawkID and password on the website, you can use your mobile phone or tablet to complete the process with a swift swipe of the finger.
The app can also generate single-use codes to complete the second step when you don’t have cellular service, which will come in handy if you travel, internationally or otherwise, to places you may lose service. If you work in an area with poor cellular or wireless reception, or if you don’t own a smart phone, an office phone or the codes are the next-best second-step verification methods.
Use of two-step verification grows
The majority of UI employees already use Two-Step Login with Duo Security to access Employee Self Service. They enrolled voluntarily to boost the security of their information, or were already required to based on their level of permissions in HR applications. The UI first implemented two-factor authentication in the spring of 2014 and has seen steady growth in adoption.
Two-step login is becoming increasingly common as more financial institutions, companies, and universities have adopted this security measure to shelter vital information and systems.
“Many UI employees embraced this IT security measure on their own, recognizing that it’s a simple way to better protect personal and institutional data,” Drews says. “Requiring Two-Step Login and eventually extending it to other critical applications will expand our protection to even more people and systems.”
Drews says she appreciates everyone’s cooperation in this important security initiative.
“Cyber criminals continually develop new ways to hijack accounts and steal valuable information, redirect funds, attack others using our name, or steal identities for profit,” she says. “As threats grow, we must add more layers of protection to safeguard our data.”